Tor, short for The Onion Router, is a tool to anonymize your web traffic.
Tor is simple to use and yet incredibly complicated under the hood. You install software, available at www.torproject.org, or a browser extension. Tor routes your data through a bunch of nodes. Each of those computers or routers is only aware of the node in front of or behind it in the communication route and encrypting the next node sent. Since each step is encrypted, these layers of encryption can be considered like a network with layers like an onion. So if each step is partially encrypted, a compromise of any device in the route will still defeat network surveillance, and because all traffic at the entry point to Tor is encrypted it’s safe to browse anonymously when using, let’s say, a conference wi-fi.
The Tor browser is one way to use Tor. Here, you can simply download the browser, install it on your computer by dragging it to /Applications, and then all traffic for that browser routes through Tor. Open https://check.torproject.org/ to verify.
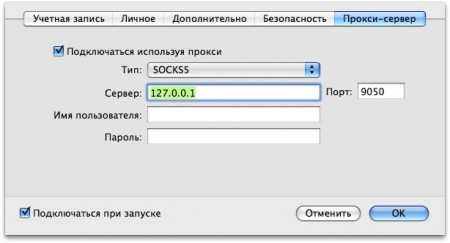
This is great for protecting web traffic. But for IRC and other traffic you usually need a little more. My favorite way to do this is to have a simple script that configures a SOCKS proxy for Tor. To do so, we’ll first install Tor, using homebrew:
brew install tor
Once installed, simply run tor at a command line and you’ll start routing traffic sent at your computer if configured appropriately:
The Tor software protects you by bouncing your communications around a distributed. There are many alternatives to Tor for Mac if you are looking to replace it. The most popular Mac alternative is Tor Browser, which is both free and Open Source.If that doesn't suit you, our users have ranked more than 100 alternatives to Tor and loads of them are available for Mac so hopefully you can find a suitable replacement. Mac tor browser free download - Tor Browser, Tor Browser Bundle, TOR Network: TOR Browser, and many more programs.
tor
Next, we’ll need to configure the SOCKS proxy. Here, we’ll do so for a network interface called Wi-Fi:
sudo networksetup -setsocksfirewallproxy Wi-Fi 127.0.0.1 9050 off
Once setup we’ll use similar syntax but adding state at the end to enable the proxy:
sudo networksetup -setsocksfirewallproxystate Wi-Fi on
Office For Mac 2016 Download
Now your traffic should be routing through tor. To check that let’s curl that check.torproject.org page from earlier:
curl --socks5 localhost:9050 --socks5-hostname localhost:9050 -s https://check.torproject.org/
You can then quickly disable that proxy and return traffic to routing normally using the same proxy command as earlier, but setting the state to off:
sudo networksetup -setsocksfirewallproxystate Wi-Fi off
Microsoft 2016 For Mac Download
Given that it’s an anonymous system, tor has been used to launch attacks. This has led a number of security products to block Tor. An example of this might be Cisco Umbrella. You don’t want to disable these types of tools too much as you’re bypassing their protections, but sometimes you just need to accomplish a quick task. So to disable that, you might run the following and reboot:
sudo mv '/Library/Application Support/OpenDNS Roaming Client/com.opendns.osx.DNSCryptProxy.plist' ~/Desktop/
Or just use launchctl to stop it. You can then move the plist back or start the event again, as needed. As Network Extensions become more of a thing this won’t work at some point in the future, but we’ll dive in later to defeat that as well, if ya’ want!
BLOCK TRACKERS
Tor Browser isolates each website you visit so third-party trackers and ads can't follow you. Any cookies automatically clear when you're done browsing. So will your browsing history.
DEFEND AGAINST SURVEILLANCE
Tor Browser prevents someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you're using Tor.
RESIST FINGERPRINTING
Tor Browser aims to make all users look the same, making it difficult for you to be fingerprinted based on your browser and device information.
MULTI-LAYERED ENCRYPTION
Your traffic is relayed and encrypted three times as it passes over the Tor network. The network is comprised of thousands of volunteer-run servers known as Tor relays.
BROWSE FREELY
With Tor Browser, you are free to access sites your home network may have blocked.
ABOUT US
We believe everyone should be able to explore the internet with privacy.We are the Tor Project, a 501(c)3 US nonprofit.We advance human rights and defend your privacy online through free software and open networks. Meet our team.
